6 open source tools for making your own VPN
Contents
- 1 6 open source tools for making your own VPN
- 1.1 SoftEther VPN Project
- 1.2 What is SoftEther VPN
- 1.3 Architecture of SoftEther VPN
- 1.4 How to Use SoftEther VPN ?
- 1.5 Ad-hoc VPN
- 1.6 LAN to LAN Bridge
- 1.7 Remote Access to LAN
- 1.8 Join a Local PC into Cloud
- 1.9 Join a Cloud VM into LAN
- 1.10 Cloud to LAN Bridge VPN
- 1.11 Cloud to Cloud Bridge VPN
- 1.12 iPhone and Android
- 1.13 Windows and Mac Laptops
- 1.14 Remote Management
- 1.15 Building Your Own Cloud
- 1.16 VPN for Network Testing, Simulation and Debugging
- 1.17 Remote Access
- 1.18 Comfortable Network Anywhere
- 1.19 Dynamic DNS and NAT Traversal
- 1.20 VPN Azure
- 1.21 Penetrates Firewall by SSL-VPN
- 1.22 Replacements of Cisco or other hardware-based VPNs
- 1.23 Replacements of OpenVPN
- 1.24 Screenshots
- 1.25 6 open source tools for making your own VPN
- 1.26 Algo
- 1.27 Streisand
- 1.28 OpenVPN
- 1.29 StrongSwan
- 1.30 SoftEther
- 1.31 WireGuard
- 1.32 Homemade VPN vs. commercial VPN
- 1.33 7 open source VPN tools for businesses
- 1.34 Benefits of OpenVPN solutions
- 1.35 The 7 best open source VPN alternatives
- 1.36 Conclusion
In early February, the Software Engineering Institute at Carnegie Mellon University posted an advisory warning stating that the Pulse Secure VPN graphic user interface failed to validate SSL certificates when connecting to websites. This left enterprise-level clients open to man-in-the-middle (and other) attacks. While the SSL validation problem has been resolved for Pulse 5.3R4.2 and Pulse 5.2R9, the Carnegie Mellon researchers still warn against using it on untrusted networks.
SoftEther VPN Project
SoftEther VPN Project develops and distributes SoftEther VPN,
An Open-Source Free Cross-platform Multi-protocol VPN Program,
as an academic project from University of Tsukuba, under the Apache License 2.0.
What is SoftEther VPN
SoftEther VPN (“SoftEther” means “Software Ethernet”) is one of the world’s most powerful and easy-to-use multi-protocol VPN software. It runs on Windows, Linux, Mac, FreeBSD and Solaris.
SoftEther VPN is open source. You can use SoftEther for any personal or commercial use for free charge.
SoftEther VPN is an optimum alternative to OpenVPN and Microsoft’s VPN servers. SoftEther VPN has a clone-function of OpenVPN Server. You can integrate from OpenVPN to SoftEther VPN smoothly. SoftEther VPN is faster than OpenVPN. SoftEther VPN also supports Microsoft SSTP VPN for Windows Vista / 7 / 8. No more need to pay expensive charges for Windows Server license for Remote-Access VPN function.
SoftEther VPN can be used to realize BYOD (Bring your own device) on your business. If you have smartphones, tablets or laptop PCs, SoftEther VPN’s L2TP/IPsec server function will help you to establish a remote-access VPN from your local network. SoftEther VPN’s L2TP VPN Server has strong compatible with Windows, Mac, iOS and Android.
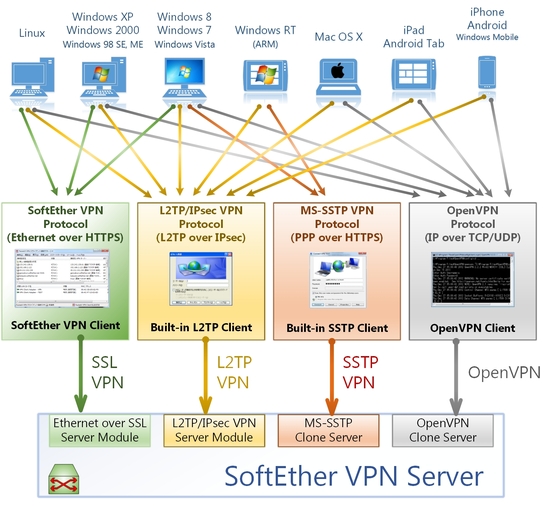
SoftEther VPN is not only an alternative VPN server to existing VPN products (OpenVPN, IPsec and MS-SSTP). SoftEther VPN has also original strong SSL-VPN protocol to penetrate any kinds of firewalls. Ultra-optimized SSL-VPN Protocol of SoftEther VPN has very fast throughput, low latency and firewall resistance.
SoftEther VPN has strong resistance against firewalls than ever. Built-in NAT-traversal penetrates your network admin’s troublesome firewall for overprotection. You can setup your own VPN server behind the firewall or NAT in your company, and you can reach to that VPN server in the corporate private network from your home or mobile place, without any modification of firewall settings. Any deep-packet inspection firewalls cannot detect SoftEther VPN’s transport packets as a VPN tunnel, because SoftEther VPN uses Ethernet over HTTPS for camouflage.
Easy to imagine, design and implement your VPN topology with SoftEther VPN. It virtualizes Ethernet by software-enumeration. SoftEther VPN Client implements Virtual Network Adapter, and SoftEther VPN Server implements Virtual Ethernet Switch. You can easily build both Remote-Access VPN and Site-to-Site VPN, as expansion of Ethernet-based L2 VPN. Of course, traditional IP-routing L3 based VPN can be built by SoftEther VPN.
![]()
SoftEther VPN has strong compatibility to today’s most popular VPN products among the world . It has the interoperability with OpenVPN, L2TP, IPsec, EtherIP, L2TPv3, Cisco VPN Routers and MS-SSTP VPN Clients. SoftEther VPN is the world’s only VPN software which supports SSL-VPN, OpenVPN, L2TP, EtherIP, L2TPv3 and IPsec, as a single VPN software.
SoftEther VPN is free software because it was developed as Daiyuu Nobori’s Master Thesis research in the University. You can download and use it from today. The source-code of SoftEther VPN is available under the Apache License 2.0.
Features of SoftEther VPN
Architecture of SoftEther VPN
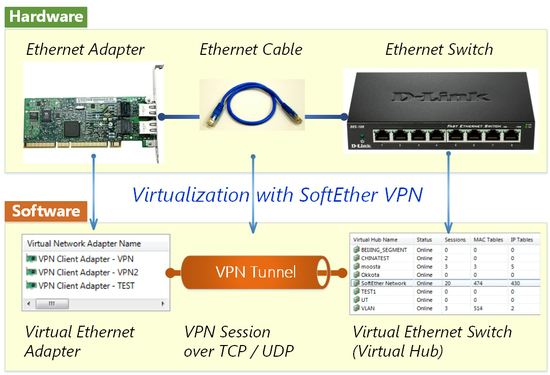
Virtualization of Ethernet devices is the key of the SoftEther VPN architecture. SoftEther VPN virtualizes Ethernet devices in order to realize a flexible virtual private network for both remote-access VPN and site-to-site VPN. SoftEther VPN implements the Virtual Network Adapter program as a software-emulated traditional Ethernet network adapter. SoftEther VPN implements the Virtual Ethernet Switch program (called Virtual Hub) as a software-emulated traditional Ethernet switch. SoftEther VPN implements VPN Session as a software-emulated Ethernet cable between the network adapter and the switch.
You can create one or many Virtual Hub with SoftEther VPN on your server computer. This server computer will become a VPN server, which accepts VPN connection requests from VPN client computers.
You can create one or many Virtual Network Adapter with SoftEther VPN on your client computer. This client computer will become a VPN client, which establishes a VPN connections to the Virtual Hub on the VPN server.
You can establish VPN sessions, as called ‘VPN tunnels’, between VPN clients and VPN servers. A VPN session is the virtualized network cable. A VPN session is realized over a TCP/IP connection. The signals through the VPN session is encrypted by SSL. Therefore, you can safely establish a VPN session beyond the Internet. A VPN session is established by SoftEther VPN’s “VPN over HTTPS” technology. It means that SoftEther VPN can create a VPN connection beyond any kinds of firewalls and NATs.
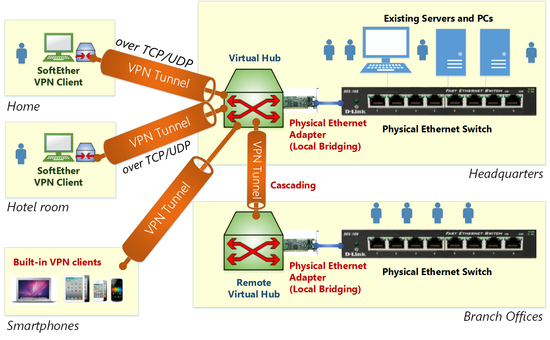
The Virtual Hub exchanges all Ethernet packets from each connected VPN session to other connected sessions. The behavior is same to traditional Ethernet switches. The Virtual Hub has a FDB (forwarding database) to optimize the transmission of Ethernet frames.
You can define a local bridge between the Virtual Hub and the existing physical Ethernet segment by using the Local Bridge function. The Local Bridge exchanges packets between the physical Ethernet adapter and the Virtual Hub. You can realize a remote-access VPN from home or mobile to the company network by using the Local Bridge function.
You can define a cascading connection between two or more remote Virtual Hubs. With cascading, you can integrate two or more remote Ethernet segments to a single Ethernet segment. For example, after you establish cascading connections between the site A, B and C, then any computers in the site A will be able to communicate with the computers in the site B and the site C. This is a site-to-site VPN.
SoftEther VPN can also establish a VPN session over UDP. The UDP-mode of SoftEther VPN supports NAT traversal. The NAT traversal function allows the VPN server behind existing NATs or firewalls to accept incoming VPN sessions. You need no network administrator’s special permission before setting up a VPN server on the company network behind firewalls or NATs. Additionally, SoftEther VPN Server may be placed on the dynamic IP address environment since SoftEther VPN has built-in Dynamic DNS (DDNS) function.
SoftEther VPN Server supports additional VPN protocols, including L2TP/IPsec, OpenVPN, Microsoft SSTP, L2TPv3 and EtherIP. These realizes the interoperability with built-in L2TP/IPsec VPN clients on iPhone, iPad, Android, Windows and Mac OS X, and also with Cisco’s VPN routers and other vendors VPN products.
How to Use SoftEther VPN ?

SoftEther VPN is an essential infrastructure to build-up IT systems on enterprises and small-businesses.
Ad-hoc VPN

Make an ad-hoc VPN consists of the small-number computers with SoftEther VPN. Despite long-distance, it is easy to communicate mutually with any kinds of LAN-oriented protocols.
LAN to LAN Bridge
Geologically distributed branches are isolated as networks by default. SoftEther VPN lays virtual Ethernet cables between your all branches. Then all computers of all branches are connected to the single LAN.
Remote Access to LAN
Does employees need to connect to the company LAN from outside or home? Remote Access VPN will realizes virtual network cable from a Client PC to the LAN from anywhere and anytime.

SoftEther VPN can build-up flexible and dependable virtual network around Clouds. Amazon EC2, Windows Azure and most of other Clouds are supporting SoftEther VPN.
Join a Local PC into Cloud
Your desktop or laptop PC can join into the Cloud VM network. You can make use of Cloud VM as if it is on your own local network easily.
Join a Cloud VM into LAN
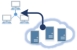
Your Cloud VM can join to your company LAN with SoftEther VPN. Anyone on your company can access to the Cloud VM without any settings.
Cloud to LAN Bridge VPN
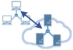
SoftEther VPN keeps a virtual dedicate Ethernet line from the Cloud to the LAN 24h/365d. You can consider remote Cloud private network as a part of your corporate network.
Cloud to Cloud Bridge VPN
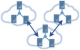
Are you using Amazon EC2 and Windows Azure, or using two or more remote datacenters of a Cloud service? SoftEther VPN can make a single united network between all Cloud VMs despite differences of physical locations.

SoftEther VPN supports several mobile devices including iPhone and Android. Your smartphone is now a part of your on-premise or Cloud network by using SoftEther VPN.
iPhone and Android

iPhone and Android has a built-in VPN client but originally they need Cisco, Juniper or other expensive hardware-based VPNs for remote-access. SoftEther VPN has a same function to Cisco, and supports your iPhone and Android easily.
Windows and Mac Laptops

Your mobile PCs with Windows or Mac can be easily connected to SoftEther VPN anywhere and anytime, despite firewalls or packet filters on Wi-Fi or overseas ISP. Windows RT is also supported.

SoftEther VPN is also an ultra-convenient tool for effective system management by IT professionals on enterprises and system integrators.
Remote Management

Are you having problem with many servers, clients and printers of your client companies are distributed around the state? SoftEther VPN will help you a network administrator as a handy tool just from your desk. You can reach to any networks by only installing SoftEther VPN.
Building Your Own Cloud
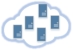
Do you want to build and provide your own Cloud service which can beat Amazon EC2 or Windows Azure? SoftEther VPN can help you to build an inter-VMs network and remote-bridging network between your Cloud and your customer’s on-premise.
VPN for Network Testing, Simulation and Debugging

SoftEther VPN is not a program only for building remote network. It can be used for network design, test, and simulation by IT professionals. For example, delay, jitter and packet loss generator is implemented on SoftEther VPN. So network designer can test VoIP phones under the bad-condition IP network.

SoftEther VPN is also convenient for home users. You can be proud of using enterprise-class VPN for your home-use.
Remote Access

Do you want to access to your home server or digital appliance from outside? Set up SoftEther VPN Server on your home PC and gain access to your server or HDTV recorder from anywhere even the opposite side of the earth, through the Internet.
Comfortable Network Anywhere

Are you a business man and running around the world? Most of Wi-Fi and local ISPs of several countries are discomfort to use because of packet filtering or censorship. So set up your private relay server on your own home PC and use it from fields to gain ease.

Does your network administrator hesitates to assign you a global IP address? Or Does your company has a firewall on the border between the private network and the Internet? No problem! SoftEther VPN has a strong function to penetrate troublesome corporate firewalls.
Dynamic DNS and NAT Traversal

Unlike legacy IPsec-based VPN, even if your corporate network doesn’t have any static global IP address you can set up your stable SoftEther VPN Server on your corporate network.
VPN Azure

If the corporate firewall is more restricted and the NAT Traversal of SoftEther VPN doesn’t work correctly, use VPN Azure to penetrate such a firewall.
IPsec-based VPN protocols which are developed on 1990’s are now obsoleted. IPsec-based VPN are not familiar with most of firewalls, NATs or proxies. Unlike IPsec-based VPN, SoftEther VPN is familiar with any kind of firewalls. Additionally SoftEther VPN requires no expensive Cisco or other hardware devices. You can replace your Cisco or OpenVPN to SoftEther VPN today.
Penetrates Firewall by SSL-VPN
Are you having trouble with IPsec-based legacy VPN products? Replace it to SoftEther VPN. SoftEther VPN Protocol is based on HTTPS so almost all kinds of firewalls will permits SoftEther VPN’s packets.
Replacements of Cisco or other hardware-based VPNs
Cisco, Juniper or other hardware-based IPsec VPNs are expensive for set-up and management. They are also lack of usability and compatibility with Firewalls. Replace them to SoftEther VPN. You can very easily replace because SoftEther VPN also has the L2TP/IPsec VPN function which is same to Cisco’s.
Replacements of OpenVPN

Are you still using OpenVPN? SoftEther VPN has more ability, better performance and easy-configurable GUI-based management tools. SoftEther VPN has also the OpenVPN Server Clone Function so that any OpenVPN clients, including iPhone and Android, can connect to SoftEther VPN easily.
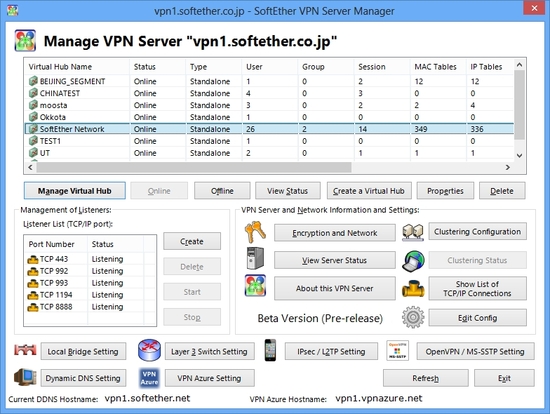
Screenshots
SoftEther VPN consists of three software: VPN Client, VPN Server and VPN Bridge.
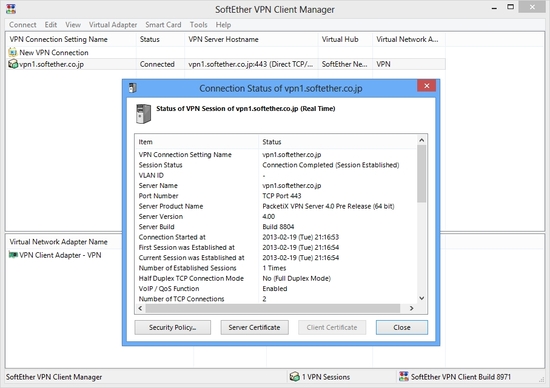
SoftEther VPN Client

SoftEther VPN Server Admin Tool
6 open source tools for making your own VPN

If you want to try your hand at building your own VPN but aren’t sure where to start, you’ve come to the right place. I’ll compare six of the best free and open source tools to set up and use a VPN on your own server. These VPNs work whether you want to set up a site-to-site VPN for your business or just create a remote access proxy to unblock websites and hide your internet traffic from ISPs.
Which is best depends on your needs and limitations, so take into consideration your own technical expertise, environment, and what you want to achieve with your VPN. In particular, consider the following factors:
- VPN protocol
- Number of clients and types of devices
- Server distro compatibility
- Technical expertise required
Algo
Algo was designed from the bottom up to create VPNs for corporate travelers who need a secure proxy to the internet. It “includes only the minimal software you need,” meaning you sacrifice extensibility for simplicity. Algo is based on StrongSwan but cuts out all the things that you don’t need, which has the added benefit of removing security holes that a novice might otherwise not notice.
More Great Content
- Free online course: RHEL technical overview
- Learn Advanced Linux Commands
- Download Cheat Sheets
- Find an Open Source Alternative
- Read Top Linux Content
- Check out open source resources
As an added bonus, it even blocks ads!
Algo supports only the IKEv2 protocol and Wireguard. Because IKEv2 support is built into most devices these days, it doesn’t require a client app like OpenVPN. Algo can be deployed using Ansible on Ubuntu (the preferred option), Windows, RedHat, CentOS, and FreeBSD. Setup is automated using Ansible, which configures the server based on your answers to a short set of questions. It’s also very easy to tear down and re-deploy on demand.
Algo is probably the easiest and fastest VPN to set up and deploy on this list. It’s extremely tidy and well thought out. If you don’t need any of the more advanced features offered by other tools and just need a secure proxy, it’s a great option. Note that Algo explicitly states it’s not meant for geo-unblocking or evading censorship, and was primarily designed for confidentiality.
Streisand
Streisand can be installed on any Ubuntu 16.04 server using a single command; the process takes about 10 minutes. It supports L2TP, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, Stunnel, Tor bridge, and WireGuard. Depending on which protocol you choose, you may need to install a client app.
In many ways, Streisand is similar to Algo, but it offers more protocols and customization. This takes a bit more effort to manage and secure but is also more flexible. Note Streisand does not support IKEv2. I would say Streisand is more effective for bypassing censorship in places like China and Turkey due to its versatility, but Algo is easier and faster to set up.
The setup is automated using Ansible, so there’s not much technical expertise required. You can easily add more users by sending them custom-generated connection instructions, which include an embedded copy of the server’s SSL certificate.
Tearing down Streisand is a quick and painless process, and you can re-deploy on demand.
OpenVPN
OpenVPN requires both client and server applications to set up VPN connections using the protocol of the same name. OpenVPN can be tweaked and customized to fit your needs, but it also requires the most technical expertise of the tools covered here. Both remote access and site-to-site configurations are supported; the former is what you’ll need if you plan on using your VPN as a proxy to the internet. Because client apps are required to use OpenVPN on most devices, the end user must keep them updated.
Server-side, you can opt to deploy in the cloud or on your Linux server. Compatible distros include CentOS, Ubuntu, Debian, and openSUSE. Client apps are available for Windows, MacOS, iOS, and Android, and there are unofficial apps for other devices. Enterprises can opt to set up an OpenVPN Access Server, but that’s probably overkill for individuals, who will want the Community Edition.
OpenVPN is relatively easy to configure with static key encryption, but it isn’t all that secure. Instead, I recommend setting it up with easy-rsa, a key management package you can use to set up a public key infrastructure. This allows you to connect multiple devices at a time and protect them with perfect forward secrecy, among other benefits. OpenVPN uses SSL/TLS for encryption, and you can specify DNS servers in your configuration.
OpenVPN can traverse firewalls and NAT firewalls, which means you can use it to bypass gateways and firewalls that might otherwise block the connection. It supports both TCP and UDP transports.
StrongSwan
You might have come across a few different VPN tools with “Swan” in the name. FreeS/WAN, OpenSwan, LibreSwan, and strongSwan are all forks of the same project, and the lattermost is my personal favorite. Server-side, strongSwan runs on Linux 2.6, 3.x, and 4x kernels, Android, FreeBSD, macOS, iOS, and Windows.
StrongSwan uses the IKEv2 protocol and IPSec. Compared to OpenVPN, IKEv2 connects much faster while offering comparable speed and security. This is useful if you prefer a protocol that doesn’t require installing an additional app on the client, as most newer devices manufactured today natively support IKEv2, including Windows, MacOS, iOS, and Android.
StrongSwan is not particularly easy to use, and despite decent documentation, it uses a different vocabulary than most other tools, which can be confusing. Its modular design makes it great for enterprises, but that also means it’s not the most streamlined. It’s certainly not as straightforward as Algo or Streisand.
Access control can be based on group memberships using X.509 attribute certificates, a feature unique to strongSwan. It supports EAP authentication methods for integration into other environments like Windows Active Directory. StrongSwan can traverse NAT firewalls.
SoftEther
SoftEther started out as a project by a graduate student at the University of Tsukuba in Japan. SoftEther VPN Server and VPN Bridge run on Windows, Linux, OSX, FreeBSD, and Solaris, while the client app works on Windows, Linux, and MacOS. VPN Bridge is mainly for enterprises that need to set up site-to-site VPNs, so individual users will just need the server and client programs to set up remote access.
SoftEther supports the OpenVPN, L2TP, SSTP, and EtherIP protocols, but its own SoftEther protocol claims to be able to be immunized against deep packet inspection thanks to “Ethernet over HTTPS” camouflage. SoftEther also makes a few tweaks to reduce latency and increase throughput. Additionally, SoftEther includes a clone function that allows you to easily transition from OpenVPN to SoftEther.
SoftEther can traverse NAT firewalls and bypass firewalls. On restricted networks that permit only ICMP and DNS packets, you can utilize SoftEther’s VPN over ICMP or VPN over DNS options to penetrate the firewall. SoftEther works with both IPv4 and IPv6.
SoftEther is easier to set up than OpenVPN and strongSwan but is a bit more complicated than Streisand and Algo.
WireGuard
WireGuard is the newest tool on this list; it’s so new that it’s not even finished yet. That being said, it offers a fast and easy way to deploy a VPN. It aims to improve on IPSec by making it simpler and leaner like SSH.
Like OpenVPN, WireGuard is both a protocol and a software tool used to deploy a VPN that uses said protocol. A key feature is “crypto key routing,” which associates public keys with a list of IP addresses allowed inside the tunnel.
WireGuard is available for Ubuntu, Debian, Fedora, CentOS, MacOS, Windows, and Android. WireGuard works on both IPv4 and IPv6.
WireGuard is much lighter than most other VPN protocols, and it transmits packets only when data needs to be sent.
The developers say WireGuard should not yet be trusted because it hasn’t been fully audited yet, but you’re welcome to give it a spin. It could be the next big thing!
Homemade VPN vs. commercial VPN
Making your own VPN adds a layer of privacy and security to your internet connection, but if you’re the only one using it, then it would be relatively easy for a well-equipped third party, such as a government agency, to trace activity back to you.
Furthermore, if you plan to use your VPN to unblock geo-locked content, a homemade VPN may not be the best option. Since you’ll only be connecting from a single IP address, your VPN server is fairly easy to block.
Good commercial VPNs don’t have these issues. With a provider like ExpressVPN, you share the server’s IP address with dozens or even hundreds of other users, making it nigh-impossible to track a single user’s activity. You also get a huge range of hundreds or thousands of servers to choose from, so if one has been blacklisted, you can just switch to another.
The tradeoff of a commercial VPN, however, is that you must trust the provider not to snoop on your internet traffic. Be sure to choose a reputable provider with a clear no-logs policy.
7 open source VPN tools for businesses
Check out these enterprise-ready, open source VPN solutions to meet the needs of any corporation, large or small.
June 8, 2018 | 1 Comment |

In recent months, many popular online security and VPN vendors have come under fire after unaddressed vulnerabilities in their products left users open to serious threats.
In early February, the Software Engineering Institute at Carnegie Mellon University posted an advisory warning stating that the Pulse Secure VPN graphic user interface failed to validate SSL certificates when connecting to websites. This left enterprise-level clients open to man-in-the-middle (and other) attacks. While the SSL validation problem has been resolved for Pulse 5.3R4.2 and Pulse 5.2R9, the Carnegie Mellon researchers still warn against using it on untrusted networks.
After suffering from similar vulnerabilities, Cisco Adaptive Security Appliance software resolved its SSL validation problems, but didn’t address whether it should be avoided on untrusted networks. These disclosures have left many organizations wondering whether they can trust these industry titans with their sensitive information or if they should abandon VPNs altogether.
Luckily, there are a number of enterprise-level, open source VPN solutions that will meet the needs of any corporation, large or small.
Benefits of OpenVPN solutions
OpenVPN is one of the power players in the online privacy world. It is an open source VPN technology that comes equipped with a 256-AES-CBC with a 2048 bit Diffie-Hellman key for Windows users. For Linux, iOS, and MacOS users, OpenVPN encrypts information via the IKEv2/IPsec protocol with an AES-256-CGM and 3072bit DH key.
In my experience, the Diffie-Hellman key is far more robust than RSA (Rivest, Shamir, and Adelman) due to the fact that it enables perfect forward secrecy, which ensures that past communications and transfers cannot be decrypted in the future even if a long-term key is compromised.
What this means is OpenVPN is one of the most secure open source VPN software options available.
Furthermore, the OpenVPN developer community is one of the most active and vocal in the online security world. Members are constantly refining and updating the software to keep up with the rapidly changing landscape of internet security.
Considering its impressive security specifications and the passionate team behind the software, I encourage corporations to use an OpenVPN-powered security solution, including some of the options on this list, whenever and wherever possible.
The 7 best open source VPN alternatives
Following are seven of the best open source VPN solutions that might work for your enterprise.
Openswan | Linux
Openswan is an IPsec implementation for Linux that supports most IPsec-related extensions (including IKEv2). It’s largely been considered the “go-to” VPN software for Linux users since early 2005. Depending on the version of Linux you are running, Openswan may already be in your distribution, and you can download the source code directly from its site if you can’t easily locate the software.
Tcpcrypt | Windows and MacOS
The Tcpcrypt protocol is a unique VPN solution in the sense that it requires no configuration, changes to applications, or noticeable shifts in your network connection. Tcpcrypt operates using something known as “opportunistic encryption.” This means if the other end of the connection communicates to Tcpcrypt, the traffic will be encrypted, otherwise, it can be seen as cleartext.
While this is far from ideal, the protocol has experienced a number of robust updates that make it more protected against both passive and active attacks. Although I would not recommend Tpcrypt as a company-wide solution, it can serve as a fantastic and easy-to-implement solution for employees and branches that handle less sensitive information.
Tinc | Linux, MacOS, and Windows
Tinc is free software that is licensed under the GNU General Public License. What sets tinc apart from the other VPNs on this list (including the OpenVPN protocol) is the variety of unique features it includes, including encryption, optional compression, automatic mesh routing, and easy expansion. These features make tinc an ideal solution for businesses that want to create a VPN out of numerous smaller networks based far apart.
SoftEther VPN | Linux, Windows, MacOS, and others
SoftEther (short for software Ethernet) VPN is by far one of the most powerful and user-friendly multi-protocol VPN software options on the market. Positioned as the ideal alternative to OpenVPN, SoftEther VPN has a clone function for the OpenVPN server allowing you to seamlessly migrate from OpenVPN to SoftEther VPN. SoftEther’s impressive security standards and capabilities are considered comparable to market leaders such as NordVPN, making it an open source powerhouse.
SoftEther is also compatible with the L2TP and IPsec protocols, enabling added customization. Furthermore, SoftEther VPN has proven to be even faster than OpenVPN, improving the browsing experience. SoftEther’s primary drawback is that it lags behind its contemporaries in terms of compatibility. However, the lead cause of this issue is the relative novelty of the SoftEther protocol and, as time goes on, you will likely see more and more platforms supporting SoftEther.
OpenConnect | Linux
Considering that OpenConnect was a VPN client created to support Cisco’s AnyConnect SSL VPN, you might be surprised to see this software on the list (after all this is an article detailing alternatives to Cisco and Pulse). However, it’s important to note that OpenConnect is not officially associated with Cisco or Pulse Secure. It’s simply compatible with their equipment.
In fact, redevelopment of OpenConnect started after a trial of the Cisco client found it to have numerous security vulnerabilities, which OpenConnect set out to rectify. Today OpenConnect has addressed all of the Cisco client deficiencies (and more), making it one of the leading Cisco alternatives for any Linux user.
Libreswan | Linux, FreeBSD, and MacOS
After more than 15 years of active development, Libreswan has created one of the best open source VPN alternatives on the modern market. Libreswan currently supports the most common VPN protocols, IPsec, IKEv1, and IKEv2. Like Tcpcrypt, Libreswan operates based on opportunistic encryption, making it vulnerable to active attacks. However, the plethora of security features and the active developer community make Libreswan a great option for low-mid grade encryption requirements.
StrongSwan | Linux, Android, and routers
Maintained by Andreas Steffen, a professor for security in communications and the head of the Institute for Internet Technologies and Applications at the Swiss University of Applied Sciences Rapperswil, strongSwan has carved a name for itself in the VPN community by offering exceptional encryption standards, easy configuration, and IPsec policies that support large and complicated VPN networks.
Conclusion
Although the recent vulnerabilities revealed in the Cisco and Pulse Secure networks are troubling (to say the least), there are numerous open source alternatives that are suitable on the enterprise level. While implementing these solutions will require significant technical savvy and a high degree of company-wide cooperation, you can sleep much sounder at night knowing your company’s sensitive information is secured by the best protocols available.
